Lost a NAS Netgear ReadyNAS on the network
A friend was not able to find his NAS on the network and we wanted to backup this data. The DHCP server of his Internet router was not providing any IP to this device.
The NAS is a Netgear ReadyNAS 102 (RN10200) with two disks in RAID 1.
I took a laptop with Silverblue.

[moore@chuwux ~]$ cat /etc/redhat-release
Fedora release 33 (Thirty Three)
[moore@chuwux ~]$ cat /etc/os-release
NAME=Fedora
VERSION="33.20201029.0 (Silverblue)"
ID=fedora
VERSION_ID=33
VERSION_CODENAME=""
PLATFORM_ID="platform:f33"
PRETTY_NAME="Fedora 33.20201029.0 (Silverblue)"
ANSI_COLOR="0;38;2;60;110;180"
LOGO=fedora-logo-icon
CPE_NAME="cpe:/o:fedoraproject:fedora:33"
HOME_URL="https://fedoraproject.org/"
DOCUMENTATION_URL="https://docs.fedoraproject.org/en-US/fedora-silverblue/"
SUPPORT_URL="https://fedoraproject.org/wiki/Communicating_and_getting_help"
BUG_REPORT_URL="https://bugzilla.redhat.com/"
REDHAT_BUGZILLA_PRODUCT="Fedora"
REDHAT_BUGZILLA_PRODUCT_VERSION=33
REDHAT_SUPPORT_PRODUCT="Fedora"
REDHAT_SUPPORT_PRODUCT_VERSION=33
PRIVACY_POLICY_URL="https://fedoraproject.org/wiki/Legal:PrivacyPolicy"
VARIANT="Silverblue"
VARIANT_ID=silverblue
OSTREE_VERSION='33.20201029.0'
First install Wireshark:
[moore@chuwux ~]$ sudo rpm-ostree install wireshark
Checking out tree fc28eee... done
Enabled rpm-md repositories: fedora-cisco-openh264 updates fedora
rpm-md repo 'fedora-cisco-openh264' (cached); generated: 2020-08-25T19:10:34Z
rpm-md repo 'updates' (cached); generated: 2020-11-27T00:49:07Z
rpm-md repo 'fedora' (cached); generated: 2020-10-19T23:27:19Z
Importing rpm-md... done
Resolving dependencies... done
Will download: 6 packages (28.4 MB)
Downloading from 'updates'... done
Downloading from 'fedora'... done
Importing packages... done
Checking out packages... done
Running pre scripts... done
Running post scripts... done
Running posttrans scripts... done
Writing rpmdb... done
Writing OSTree commit... done
Staging deployment... done
Freed: 121.1 MB (pkgcache branches: 0)
Added:
compat-lua-libs-5.1.5-17.fc33.x86_64
libsmi-0.4.8-27.fc33.x86_64
openal-soft-1.19.1-9.fc33.x86_64
qt5-qtmultimedia-5.15.1-1.fc33.x86_64
wireshark-1:3.2.7-2.fc33.x86_64
wireshark-cli-1:3.2.7-2.fc33.x86_64
Run "systemctl reboot" to start a reboot
Yes you have to reboot if you install one application, but I love this immutable operating system.
[moore@chuwux ~]$ systemctl reboot
We can launch, if needed the Wireshark application:

I plug a Belkin USB-C to Gigabit Ethernet Adapter (F2CU040):
[moore@chuwux ~]$ lsusb | grep RTL8153
Bus 004 Device 003: ID 0bda:8153 Realtek Semiconductor Corp. RTL8153 Gigabit Ethernet Adapter
I plug a crossover cable between the NAS and the laptop.

[moore@chuwux ~]$ sudo tshark -D
Running as user "root" and group "root". This could be dangerous.
1. wlp1s0
2. enp0s20f0u1
3. lo (Loopback)
4. any
5. bluetooth-monitor
6. nflog
7. nfqueue
8. bluetooth0
9. usbmon0
10. usbmon1
11. usbmon2
12. ciscodump (Cisco remote capture)
13. dpauxmon (DisplayPort AUX channel monitor capture)
14. sdjournal (systemd Journal Export)
15. sshdump (SSH remote capture)
16. udpdump (UDP Listener remote capture)
I can capture the trafic on this interface.
I can seen that the NAS is broadcasting DHCP requests:
[moore@chuwux ~]$ sudo tshark -i enp0s20f0u1
Running as user "root" and group "root". This could be dangerous.
Capturing on 'enp0s20f0u1'
1 0.000000000 0.0.0.0 → 255.255.255.255 DHCP 318 DHCP Discover - Transaction ID 0x6c32c41b
2 0.001525476 :: → ff02::16 ICMPv6 110 Multicast Listener Report Message v2
= 3 0.388667945 :: → ff02::16 ICMPv6 110 Multicast Listener Report Message v2
4 0.580790405 :: → ff02::1:ff9c:80c ICMPv6 86 Neighbor Solicitation for fe80::e9aa:e30a:299c:80c
5 1.604954588 fe80::e9aa:e30a:299c:80c → ff02::16 ICMPv6 110 Multicast Listener Report Message v2
6 1.607582965 fe80::e9aa:e30a:299c:80c → ff02::16 ICMPv6 90 Multicast Listener Report Message v2
7 1.612597951 fe80::e9aa:e30a:299c:80c → ff02::16 ICMPv6 130 Multicast Listener Report Message v2
8 1.789270586 fe80::e9aa:e30a:299c:80c → ff02::2 ICMPv6 62 Router Solicitation
9 1.862055773 fe80::e9aa:e30a:299c:80c → ff02::fb MDNS 199 Standard query response 0x0000 PTR, cache flush linux.local AAAA, cache flush fe80::e9aa:e30a:299c:80c
10 2.013546740 fe80::e9aa:e30a:299c:80c → ff02::16 ICMPv6 130 Multicast Listener Report Message v2
11 2.293376678 0.0.0.0 → 255.255.255.255 DHCP 318 DHCP Discover - Transaction ID 0xb285d8d6
12 2.564781831 fe80::e9aa:e30a:299c:80c → ff02::16 ICMPv6 130 Multicast Listener Report Message v2
13 3.101893204 fe80::e9aa:e30a:299c:80c → ff02::fb MDNS 180 Standard query 0x0000 PTR _nfs._tcp.local, "QM" question PTR _ftp._tcp.local, "QM" question PTR _webdav._tcp.local, "QM" question PTR _webdavs._tcp.local, "QM" question PTR _sftp-ssh._tcp.local, "QM" question PTR _smb._tcp.local, "QM" question PTR _afpovertcp._tcp.local, "QM" question
14 3.916972211 fe80::e9aa:e30a:299c:80c → ff02::fb MDNS 199 Standard query response 0x0000 PTR, cache flush linux.local AAAA, cache flush fe80::e9aa:e30a:299c:80c
15 5.793472408 fe80::e9aa:e30a:299c:80c → ff02::2 ICMPv6 62 Router Solicitation
16 6.399686362 0.0.0.0 → 255.255.255.255 DHCP 318 DHCP Discover - Transaction ID 0x5a2e5158
17 7.104263727 fe80::e9aa:e30a:299c:80c → ff02::fb MDNS 180 Standard query 0x0000 PTR _nfs._tcp.local, "QM" question PTR _ftp._tcp.local, "QM" question PTR _webdav._tcp.local, "QM" question PTR _webdavs._tcp.local, "QM" question PTR _sftp-ssh._tcp.local, "QM" question PTR _smb._tcp.local, "QM" question PTR _afpovertcp._tcp.local, "QM" question
18 11.142591783 fe80::e9aa:e30a:299c:80c → ff02::16 ICMPv6 130 Multicast Listener Report Message v2
19 11.177752875 fe80::e9aa:e30a:299c:80c → ff02::16 ICMPv6 130 Multicast Listener Report Message v2
20 11.847460923 :: → ff02::16 ICMPv6 90 Multicast Listener Report Message v2
21 11.897532683 :: → ff02::1:ff36:7e1b ICMPv6 78 Neighbor Solicitation for fe80::2ac6:8eff:fe36:7e1b
22 12.502623353 0.0.0.0 → 255.255.255.255 DHCP 342 DHCP Discover - Transaction ID 0x58f33835
23 12.737582654 :: → ff02::16 ICMPv6 90 Multicast Listener Report Message v2
24 12.897587086 fe80::2ac6:8eff:fe36:7e1b → ff02::16 ICMPv6 90 Multicast Listener Report Message v2
25 12.897587710 fe80::2ac6:8eff:fe36:7e1b → ff02::2 ICMPv6 70 Router Solicitation from 28:c6:8e:36:7e:1b
26 13.227424165 fe80::2ac6:8eff:fe36:7e1b → ff02::16 ICMPv6 90 Multicast Listener Report Message v2
27 15.038989038 0.0.0.0 → 255.255.255.255 DHCP 318 DHCP Discover - Transaction ID 0xa9e58e89
28 15.039896808 0.0.0.0 → 255.255.255.255 DHCP 342 DHCP Discover - Transaction ID 0x58f33835
29 15.106419781 fe80::e9aa:e30a:299c:80c → ff02::fb MDNS 180 Standard query 0x0000 PTR _nfs._tcp.local, "QM" question PTR _ftp._tcp.local, "QM" question PTR _webdav._tcp.local, "QM" question PTR _webdavs._tcp.local, "QM" question PTR _sftp-ssh._tcp.local, "QM" question PTR _smb._tcp.local, "QM" question PTR _afpovertcp._tcp.local, "QM" question
30 16.907786720 fe80::2ac6:8eff:fe36:7e1b → ff02::2 ICMPv6 70 Router Solicitation from 28:c6:8e:36:7e:1b
31 18.047990392 0.0.0.0 → 255.255.255.255 DHCP 342 DHCP Discover - Transaction ID 0x58f33835
32 20.917952987 fe80::2ac6:8eff:fe36:7e1b → ff02::2 ICMPv6 70 Router Solicitation from 28:c6:8e:36:7e:1b
33 21.058065926 0.0.0.0 → 255.255.255.255 DHCP 342 DHCP Discover - Transaction ID 0x58f33835
34 24.068291447 0.0.0.0 → 255.255.255.255 DHCP 342 DHCP Discover - Transaction ID 0x58f33835
35 31.108123326 fe80::e9aa:e30a:299c:80c → ff02::fb MDNS 180 Standard query 0x0000 PTR _nfs._tcp.local, "QM" question PTR _ftp._tcp.local, "QM" question PTR _webdav._tcp.local, "QM" question PTR _webdavs._tcp.local, "QM" question PTR _sftp-ssh._tcp.local, "QM" question PTR _smb._tcp.local, "QM" question PTR _afpovertcp._tcp.local, "QM" question
36 31.534979065 0.0.0.0 → 255.255.255.255 DHCP 318 DHCP Discover - Transaction ID 0x3c42ec21
37 44.814538784 :: → ff02::16 ICMPv6 150 Multicast Listener Report Message v2
38 44.848264081 0.0.0.0 → 255.255.255.255 DHCP 318 DHCP Discover - Transaction ID 0xbc480a2a
39 44.849532371 :: → ff02::16 ICMPv6 150 Multicast Listener Report Message v2
40 44.932592220 :: → ff02::1:ff9c:80c ICMPv6 86 Neighbor Solicitation for fe80::e9aa:e30a:299c:80c
41 45.316746536 :: → ff02::16 ICMPv6 130 Multicast Listener Report Message v2
42 45.956970398 fe80::e9aa:e30a:299c:80c → ff02::16 ICMPv6 110 Multicast Listener Report Message v2
43 45.961579551 fe80::e9aa:e30a:299c:80c → ff02::16 ICMPv6 130 Multicast Listener Report Message v2
44 45.961840438 fe80::e9aa:e30a:299c:80c → ff02::2 ICMPv6 62 Router Solicitation
45 46.380738998 fe80::e9aa:e30a:299c:80c → ff02::16 ICMPv6 130 Multicast Listener Report Message v2
46 46.452644882 fe80::e9aa:e30a:299c:80c → ff02::16 ICMPv6 130 Multicast Listener Report Message v2
47 46.624130105 fe80::e9aa:e30a:299c:80c → ff02::fb MDNS 199 Standard query response 0x0000 PTR, cache flush linux.local AAAA, cache flush fe80::e9aa:e30a:299c:80c
48 46.892115821 0.0.0.0 → 255.255.255.255 DHCP 318 DHCP Discover - Transaction ID 0xfc5ef73f
49 47.950825409 fe80::e9aa:e30a:299c:80c → ff02::fb MDNS 180 Standard query 0x0000 PTR _nfs._tcp.local, "QM" question PTR _ftp._tcp.local, "QM" question PTR _webdav._tcp.local, "QM" question PTR _webdavs._tcp.local, "QM" question PTR _sftp-ssh._tcp.local, "QM" question PTR _smb._tcp.local, "QM" question PTR _afpovertcp._tcp.local, "QM" question
50 48.636798669 fe80::e9aa:e30a:299c:80c → ff02::fb MDNS 199 Standard query response 0x0000 PTR, cache flush linux.local AAAA, cache flush fe80::e9aa:e30a:299c:80c
51 49.792737860 fe80::e9aa:e30a:299c:80c → ff02::2 ICMPv6 62 Router Solicitation
52 51.218093763 0.0.0.0 → 255.255.255.255 DHCP 318 DHCP Discover - Transaction ID 0x8223d441
53 51.952862765 fe80::e9aa:e30a:299c:80c → ff02::fb MDNS 180 Standard query 0x0000 PTR _nfs._tcp.local, "QM" question PTR _ftp._tcp.local, "QM" question PTR _webdav._tcp.local, "QM" question PTR _webdavs._tcp.local, "QM" question PTR _sftp-ssh._tcp.local, "QM" question PTR _smb._tcp.local, "QM" question PTR _afpovertcp._tcp.local, "QM" question
^C53 packets captured
So the NAS didn’t have an issue and I can try to use this device on my network.
The NAS can get one IP from my local DHCP server.
I can connect to the UI of the NAS.
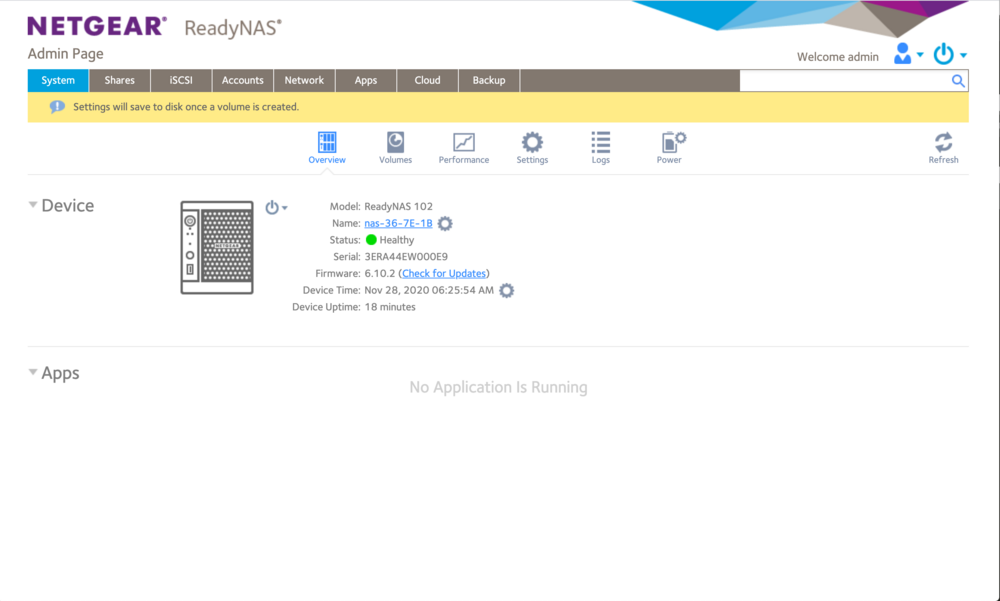
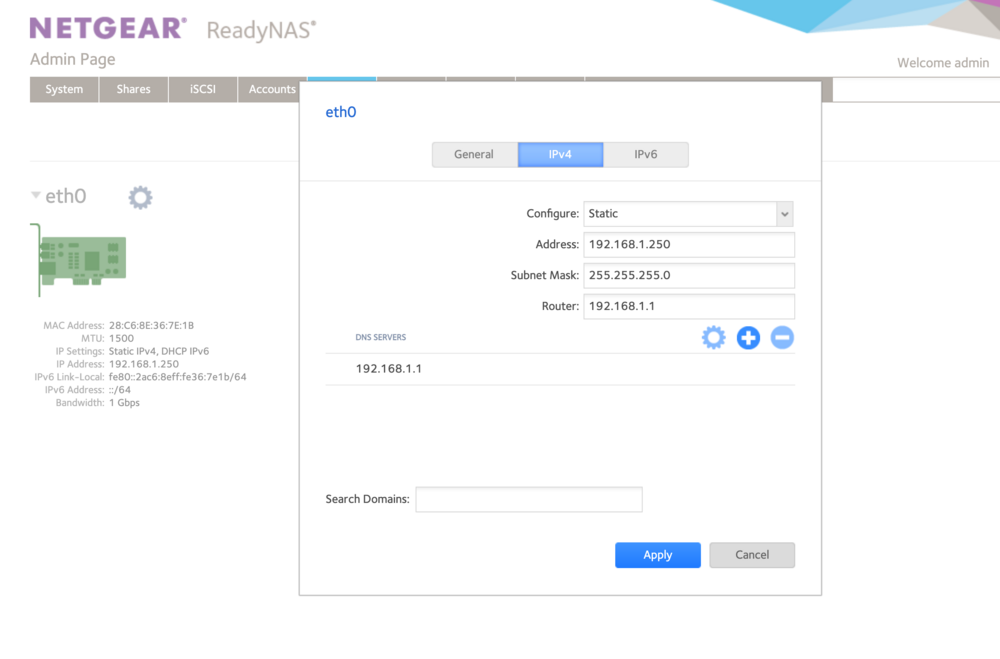
I force one IP before giving back this device to my friend.
Wireshark is Swiss knife that can help to do deep dive debugging.
